Gtalk Vs Window Media Player Troubleshooting
Posted by nikhil Labels: Google, Windows Tips And Tricks1-)just copy the URL of that song and
2-)paste it on the website www.keepvid.com
3-)click on the download option and u will get a choice to
4-)download in any of two format i.e. FLV and MP4
click on your choice and u r done!!!!
1. Right-click on any shortcut you have to IE
[You should create a shortcut out of your desktop IE icon, and delete the original icon]
2. Click Properties
3. Add ' -nohome' [with a space before the dash] after the endquotes in the Target field.
4. Click OK
Fire up IE from your modified shortcut, and be amazed by how fast you are able to use IE!
~ cheers ~ (it works)
INTERNET EXPLORER SPEED UP.
Edit your link to start Internet Explorer to have -nohome after it. For Example: "C:\Program Files\Internet Explorer\IEXPL
Here is a simple trick how to hide ur folder from everyone
just follow the simple steps and you are in..
1.right click on the folder which u hav to hide
2.rename it by pressing alt type 255 with num pad.
3.again right click on the folder
4.go to properties switch to customize option.
5.go to chose icon option
and choose the 13 cloumn thid row option.
thats it !!!!
NOTE:- for more safety just switch its attributes to hidden.
To Retrive Unsaved Number(SE K810i)
Posted by rehaan Labels: Mobile Stuff, SONY ERICSSON 240 X 320 USERSwell it is a tym when u want to retrive unsaved number....
so here is the simple procedure to do so for sony ericsson K810i users.
1.go to msg
2.go to write msg
3.then go to send option
4.go to contacts.
5.right click u will see the four options click the unsaved number option .
and u r done man...........
1 MILLION SERIALS (2009 ORIGINAL VERSION)
Posted by nikhil Labels: Premium Accounts And Passwords, Windows Tips And TricksWindows Vista SP2 Final Lite Edition Ultimate+Home Premium in 1 CD | 699 MB
Posted by nikhil Labels: Windows Tips And Tricks2. Spam blogs ( To get traffic and authority)
Your bandwidth
Duplicate posts
Search engine ranking
Image hotlinking
The point here is if someone if copying your blog, you should take it seriously. The first approach should be contacting the author and make them understand the concept of plagiarism.
In most of the case this works. If not, you can report to the advertisement partner of that blog or the hosting company of the blog.
To make your work easier I’m pointing out few hosts along with the contact page to report abuse
Hosting
Report Link
Blogspot
Blogspot spam
Wordpress.com
Wordpress.com spam
blog.co.in
blog.co.in abuse
Dreamhost
Dreamhost Spam
Adsense
Adsense Abuse reporting
Youtube
Youtube Spam
By reporting spam, you are actually participating in the blogging community effort to keep it clean.
Click Start Run and type cmd to open a command prompt.
At the prompt, type systeminfo
Scroll down the list of information to the line that says System Up Time.
This will tell you in days, hours, minutes and seconds how long the system has been up.
Note that this command only works in XP Pro, not in XP Home. You can, however, type net statistics workstation at the prompt in Home. The first line will tell you the day and time that the system came online.
This is a very big and not known if its bad(steal banking info) or half bad (spam)
But its spread itself everywhere
and is yet to activate
A lot of hard working researchers have made this simple webpage to test if you are infected
http://www.confickerworkinggroup.org/infection_test/cfeyechart.html



WHAT IS TROJAN AND VIRUS?
What is a Virus?
A virus is a manmade program or piece of code that causes an unexpected, usually negative, event. Viruses are often disguised games or images with clever marketing titles such as "Me, nude."
What is a Worm?
Computer Worms are viruses that reside in the active memory of a computer and duplicate themselves. They may send copies of themselves to other computers, such as through email or Internet Relay Chat (IRC).
What is a Trojan Horse?
A Trojan horse program is a malicious program that pretends to be a benign application; a Trojan horse program purposefully does something the user does not expect. Trojans are not viruses since they do not replicate, but Trojan horse programs can be just as destructive. Many people use the term to refer only to non-replicating malicious programs, thus making a distinction between Trojans and viruses.
Anti Copy Personal - Prevent Unauthorised Copying (8mb only) A Must Have
Posted by rehaan Labels: Windows Tips And Tricks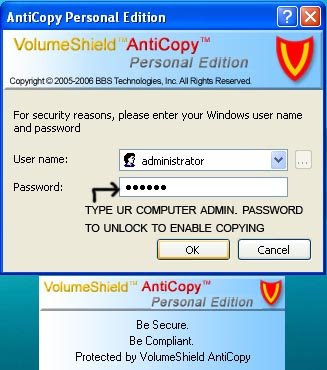
So Here's the Solution for it.
Without Your Password, Nobody Can Copy Your Files Away!!
AntiCopy Personal Edition is an useful software that provides complete protection against
data theft from personal or laptop computers.
Worried about someone stealing your personal documents, or your contact list?
With Personal Edition, you are able to prevent the attachment of unauthorized portable
storage devices, keep a log of all device use, and 'whitelist' your own frequently used devices.
AntiCopy Personal edition provides you with the confidence that your computer is shielded
from data theft no matter where you are
DOWNLOAD LINK:-
http://rapidshare.com/files/205599393/Anticopy.Personal.Ed.v2009_Cw_lee.rar
Search What You Want
Posted by rehaan Labels: Google, Premium Accounts And Passwords, Windows Tips And Tricks


http://www.keyboardr.com/
http://www.whereisdoc.com/
(A boon for students!)
http://www.justhearit.com/
(For music freaks)
And finally, someone who claims itself better than google!
http://www.cuil.com/




























